News
COVID-19 is both a health crisis and economic crisis. Lockdowns caused GDP to plunge 12% in the EU and 33% in the US in the second quarter of 2020.
Experts rank durable mass unemployment first, and think that, in the long term, younger people who are just entering the job market are likely to be affected most.
In the UE, macroeconomic risk is felt most acutely in Spain, followed by Mexico. Unemployment in the US has risen to above 10%; notwithstanding, just a few US experts consider macroeconomic risk to be important (*).
By other hand, financial risks have also risen up. Global net public debt is expected to rise to 85.3% this year from 69.4% last year. This will change the playing field for younger generations, who will inherit unprecedented levels of debt. In the future, when normal monetary policy resumes, it may cause a crisis particularly hard for emerging markets.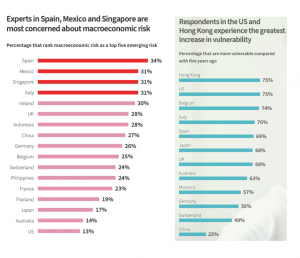
(*) AXA Future Risk Report
Experts think that risks will continue to force governments to respond to and recover from shocks that are already realized and prevent and mitigate the impact of those that are still to come. Insufficient responses will prolong the economic and financial damage from the pandemic and, in some cases, will cause political instability as dissatisfied citizens punish ineffective governments.
Beyond health, the pandemic is acting as an accelerant of existing geopolitical themes and trends. These pre-existing trends now accelerated by COVID-19 include the trajectory of China’s relationship with the world (and especially the United States), technology competition, supply chain reordering, policy responses to global climate change, nationalist and protectionist policies, and the role and appropriate use of industrial policy, among many other themes.
In words of Renaud Guidée (AXA Group Chief Risk Officer), “The pandemic has exacerbated inequality. The fact that white-collar workers could safely work from home during lockdowns, but blue-collar workers couldn’t, and were therefore more exposed to the virus, symbolized this. It’s another factor that may undermine social cohesion in many Western countries.”
The pandemic has showcased the strength of the internet, despite some early concerns about how telecommunication and data networks would handle substantially increased loads, in general, internet infrastructure has held up well during the crisis. Cybersecurity has fallen one place to be the third-most- important risk to society, but it is still considered to be a major threat. Despite this notable success, business continuity is now increasingly reliant on a small number of influential technology companies. As lockdowns took hold, previously unknown videoconferencing apps became household names overnight, as millions of companies and households came to rely on their services to conduct business and stay in touch with friends and family.
Geopolitical risk drives businesses to reassess supply chains; so that, many of them are looking at their supply chains, reducing their dependency on certain suppliers, or suppliers from particular countries, and creating more flexible and/or regionalized supply chains. By other side, many governments around the world have taken ownership stakes in strategically important businesses to prevent them from going bankrupt during the pandemic. With greater control of businesses, they may be tempted to use protectionist measures.
